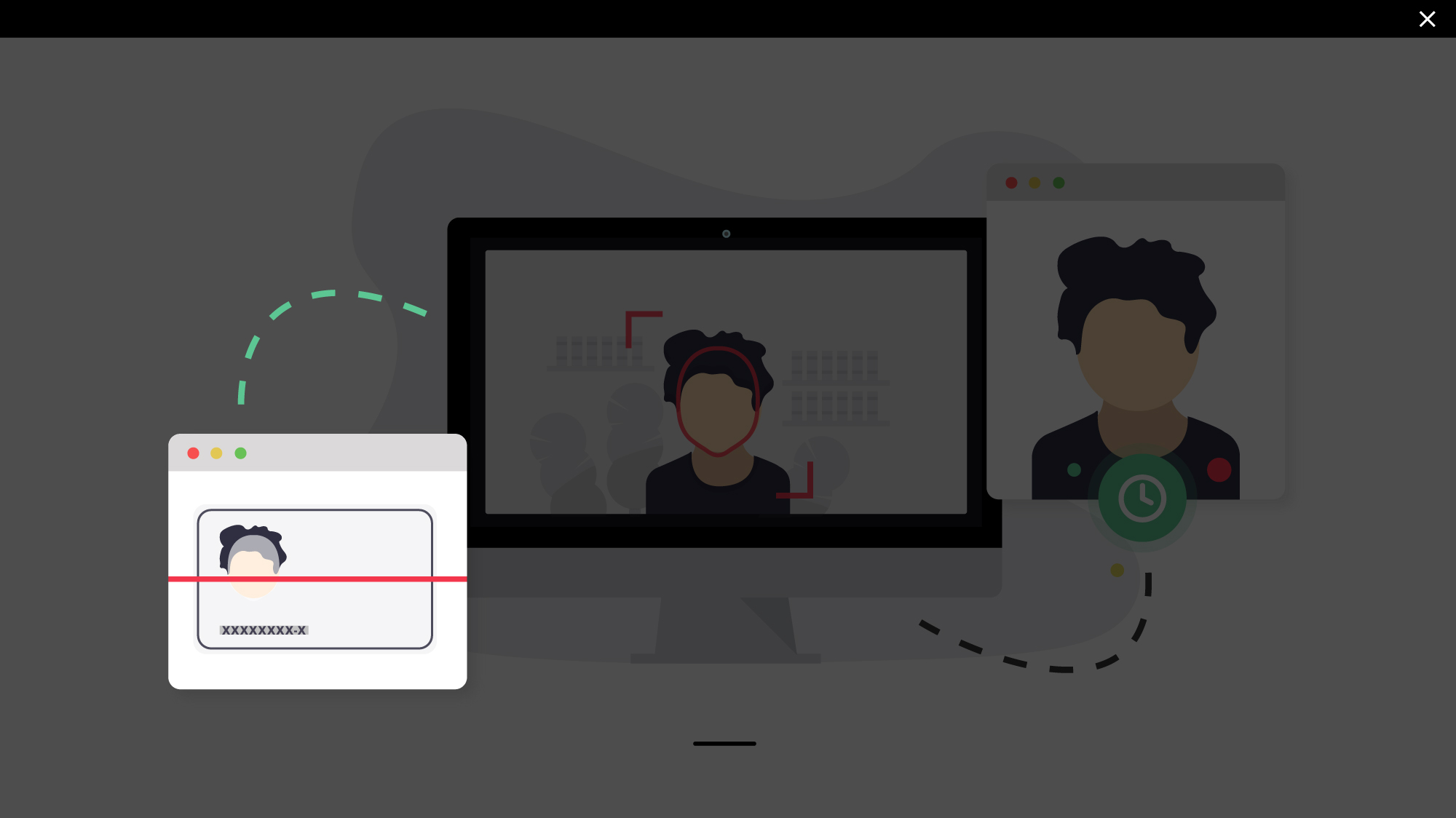
What can Tecalis Identity do for your business and clients?
Tecalis Identity has an advanced biometric facial recognition system that contrasts the customer's image obtained with the webcam or mobile device's camera with the one on the identity card or passport, making the user's identity verification process fast, simple, and intuitive.
Our technology is specially prepared for correct and reliable validation of a user's appearance: it checks the color, depth, and characteristics of the person's face that avoids the use of photocopies and other non-expert manipulations; fonts and field alignment, edge curvature radii, and rejecting invalid or deteriorated documents.
Tecalis Identity offers secure mechanisms for the correct verification and MRZ and check digit validation of identity documents, thus determining the consistency of the information extracted to verify that the information between the front and back of the identity document matches, the date format is correct and the document has not expired, thus subjecting them to a strict verification process in order to ensure the authenticity of the document and the data used for the recognition of the user's identity.
In addition, Tecalis Identity has an edge structure and technology for the correct validation of laser marks and holograms, elements that guarantee the authenticity of the document present in the document under normal light (not infrared or ultraviolet).
Many web applications have resources that are only available to certain authenticated users. Tecalis Identity allows users to be reliably identified and authenticated to confirm their identity when digitally accessing a given service, ensuring the confidentiality and availability of information only to authorized persons.
Our technology is specially designed to efficiently manage access to protected resources and determine whether a user is authorized to access those resources, verifying:
- That only authorized persons can access certain resources (systems, equipment, programs, applications, databases, networks, etc...) for their job functions.
- That accesses are identified and audited, establishing internal security controls.
- That the procedures for access to the different applications that process personal data are documented.
- That access is controlled from different aspects: network, systems, and applications.
98%
of success rate on the first attempt
Maximize user experience
Thanks to the most advanced biometric recognition technology, the facial image extraction process is robust and highly reliable, achieving high success rates on the first attempt, regardless of the light conditions during the process.
45''
of average verification time
A really high verification speed
Tecalis identity offers a biometric recognition process that stands out for its amazing speed and incredible simplicity, maximizing the user experience in the process of user identity recognition and achieving really high verification speeds.
190+
supported country documents
With full legal validity
All data circulating through this platform are encrypted and encoded, complying with the most rigorous security standards. In addition, Tecalis Signature complies with both European and American legislation.


Authentication of the operation, verification of personal data, and information reporting through APIs.
Fast OCR and facial verification process
Sending pattern, not image
Reduced pattern weight
Encrypted and tokenized pattern
Photo and video detector
Compatible with every ID documents and passports
ID card validation at fraud level
Passive Liveness
AI-Powered
Facial biometrics systems developed at Tecalis Identity allow identifying a person by analyzing the different points of his face.
The extraction of this information is currently linked to sophisticated mathematical processes and matching algorithms based on artificial intelligence to carry out a comparison (1:N) of biometric features. Basically, the system tells who the identified user is. For this, the facial pattern extracted during the process is compared against the entire user database of the system in an automated and intelligent way. For document reading, we first apply Sobel filtering to obtain an approximation of the contours of the image received through the webcam. Subsequently, the system discretizes this result by applying an arbitrary limit to obtain the morphological skeleton of the image in order to clearly distinguish the edges of the objects in the image, thus being able to confirm that we have the document centered in front of our webcam.
In the last phase, we start the information capture, making use of neural networks developed for this purpose (reading mrz codes and facial detection), with which the system extracts the information from the document. If the comparison is correct, we obtain the user whose pattern stored in the database matches or most closely resembles the pattern obtained in the extraction of facial features.
Tecalis Identity biometric recognition is performed within 6 phases:
Take the next step and get started with Tecalis Identity today
Get advice on the advantages of Tecalis Identity
Big companies already trust us
- Study your use case and give you valuable advice.
- Assist you free of charge in the use of the demo version.
- Solve other doubts (functionalities, API integration,...).